TitleBytes News & Happenings
ALTA Alert: Watch for Fake Dropbox Emails Sharing ‘Closing Disclosure’
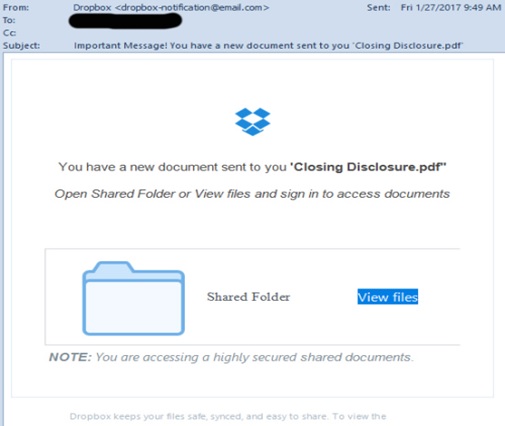
Fake Dropbox emails are circulating once again urging recipients to sign in to access and view documents.
Prior to implementation of the TILA-RESPA Integrated Disclosures (TRID) rule, the fraudulent emails were infected with a file called “final HUD-1.” In this scam, the email says that “You have a new document sent to you ‘Closing Disclosure.pdf”.
If you hover over the embedded icon, a Russian URL appears. These phishing attacks are another example of social engineering that easily fools people into sharing login details that open the door to private information. Dropbox is vulnerable to these common attacks as it was not originally designed with enterprise security in mind.
Tips to guard against phishing scams such as this one:
• Be wary of emails that ask you to view or download files from people you do not know.
• Also be cautions of emails that ask you to view files on services that you do not subscribe to.
• Hover your mouse over the URL of links contained in emails to check their destination address. Don’t click suspicious links. To log into a service like Dropbox, open a new web browser and type in the URL manually.
• Be wary of services that ask you to provide log-in credentials for a number of different email providers. This is a trick scammers use to a widen their phishing net, allowing them to steal details from users.
• Dropbox has its own webpage that educates readers on how to avoid phishing and malware scams.
You can prevent your business from receiving phishing scams by using cloud-based email-filtering and web-filtering software, which intercepts these emails before getting into your inbox.
ALTA title professionals should be vigilant when receiving and responding to email. To protect yourself, do not open attachments or click links included in suspicious email. You should also not respond or even “unsubscribe” to messages that seem suspicious. Report suspicious email to the Federal Bureau of Investigation Internet Crime Complaint Center.
Here’s a sample of the latest Dropbox email scam: